3 Securely propagating code
Particularly in military applications, it may not be desirable for anyone else than the owner to reprogram a WSN. Therefore, the base station should authenticate itself and sign its code. However, with the limited resources of nodes, public key schemes should be used sparingly. Using a global shared secret is not safe enough, because an attacker may compromise a node and capture the key.
[Jin06] proposes to use a hash chain. Only the first packet is signed with a private key. Each packet then contains a code segment and the hash of the next packet. Because the first packet is signed, that segment and hash are correct. If the second packet matches the hash, the second segment and the hash of the third packet are correct, and so on.
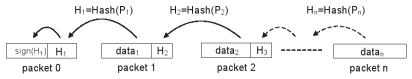
This method successfully secures the code and verifies each packet instantly. This way, packets do not have to be stored awaiting verification, which an attacker can use to do a DoS attack. However, the packets must arrive in order, something not needed by protocols as described in section 2.
To solve this problem, [Jin06] changes the protocol to make use of a hash tree. With a hash tree, each packet contains  hashes. Any of these
hashes. Any of these  packets can be verified, which in turn can verify other packets. This way, a tree of packets is built which verify each other. By sending packets by traversing the tree breadth-first, the node has a relatively long period to recover the lost packet. This method does not allow the packets to arrive in any order, but would work well when the packets are slightly out of order.
packets can be verified, which in turn can verify other packets. This way, a tree of packets is built which verify each other. By sending packets by traversing the tree breadth-first, the node has a relatively long period to recover the lost packet. This method does not allow the packets to arrive in any order, but would work well when the packets are slightly out of order.